Old Sailor, 21 November 2020.
In late 2018 United States (U.S.) Government Accountability Office (GAO) produced an interesting report on cybersecurity in U.S. DOD Weapon Systems. It's relevant to the future Canadian Surface Combatant (CSC), as the CSC Project is entering Definition phase, moving on from Requirements to actual Systems Design and Implementation. Here are some extracts from the report:
WEAPON SYSTEMS CYBERSECURITY
DOD Just Beginning to Grapple with Scale of Vulnerabilities
GAO-19-128: Published: Oct 9, 2018. Publicly Released: Oct 9, 2018.
https://www.gao.gov/products/GAO-19-128#summary
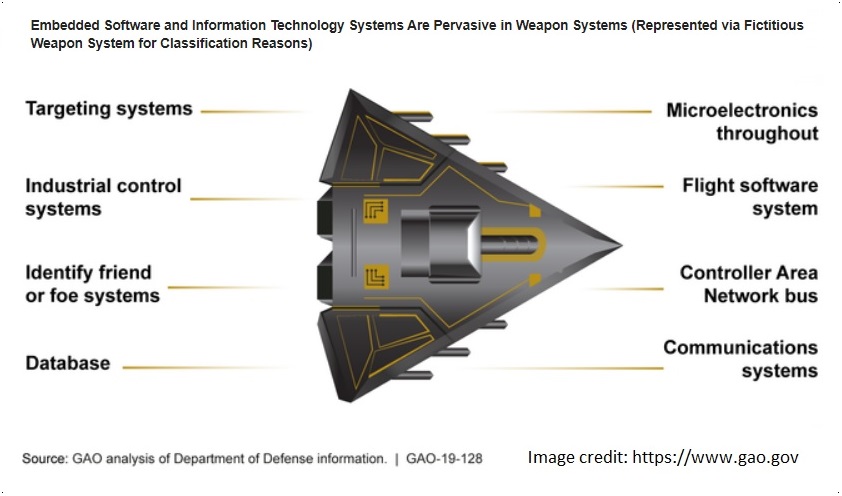
"Automation and connectivity are fundamental enablers of DOD’s modern military capabilities. However, they make weapon systems more vulnerable to cyber attacks. […] Nearly all weapon system functions are enabled by computers - ranging from basic life support functions, such as maintaining stable oxygen levels in aircraft, to intercepting incoming missiles. […] For example, the Navy has sought to reduce ship crew size based, in part, on the assumption that some manual tasks could be automated and fewer people would be needed to operate a ship [1]."
"DOD’s weapon systems are increasingly dependent on software and IT to achieve their intended performance. The amount of software in today’s weapon systems is growing exponentially and is embedded in numerous technologically complex subsystems, which include hardware and a variety of IT components."
"Weapon systems are dependent on external systems, such as positioning [GPS] and navigation systems and command and control systems in order to carry out their missions - and their missions can be compromised by attacks on those other systems. A successful attack on one of the systems the weapon depends on can potentially limit the weapon’s effectiveness, prevent it from achieving its mission, or even cause physical damage and loss of life."
"In operational testing, DOD routinely found mission-critical cyber vulnerabilities in systems that were under development, yet program officials GAO met with believed their systems were secure and discounted some test results as unrealistic."
"[During an exercise] One test team emulated a denial of service attack by rebooting the system, ensuring the system could not carry out its mission for a short period of time [2]. […] Test teams were able to defeat weapon systems cybersecurity controls meant to keep adversaries from gaining unauthorized access to the systems. […] They could see, in real-time, what the operators were seeing on their screens and could manipulate the system. They were able to [remotely] disrupt the system and observe how the operators responded."
"DOD, [as directed by Congress], has recently taken several steps to improve weapon systems cybersecurity, including issuing and revising policies and guidance to better incorporate cybersecurity considerations. […] However, DOD faces barriers that could limit the effectiveness of these steps, such as cybersecurity workforce challenges and difficulties sharing information and lessons about vulnerabilities."
Read the full document at: https://www.gao.gov/assets/700/694913.pdf
References:
- GAO, Navy Force Structure: Actions Needed to Ensure Proper Size and Composition of Ship Crews, GAO-17-413 (Washington, D.C.: May 18, 2017);
- A denial of service attack [DoS or DDoS] prevents or impairs authorized use of networks, systems, or applications by exhausting resources.